CodeHS Exploit Report
December 10, 2024
6 minute read
CodeHS is a website that provides computer science curriculum to schools and students. It is used by many schools across the United States, and is a great resource for learning programming. The platform offers a variety of courses ranging from introductory programming to more advanced topics such as data structures and algorithms. It includes interactive coding exercises, video tutorials, and a supportive community of educators and learners. However, despite its many strengths, CodeHS is not without its flaws.
In this report, I will detail a few exploits that I have uncovered in the CodeHS platform, which could potentially be used to bypass certain restrictions as well as gain unauthorized access to resources. These exploits highlight the importance of continuous security assessments and improvements to ensure the safety and academic integrity of educational tools.
Exploit 1: Unauthorized Access to Solutions
Under normal circumstances, CodeHS provides students with access to solutions to coding exercises only after they have completed the exercise themselves. This is to encourage students to think critically and solve problems on their own before seeking help. However, I have discovered a way to bypass this restriction and gain access to solutions without completing the exercise.
It appears CodeHS sends possible solutions to the client, easily accessible through the browser’s developer tools. This is a major security flaw, as it allows students to cheat by viewing the solutions before attempting the exercise themselves. This exploit could be used to gain an unfair advantage in assessments and tests.
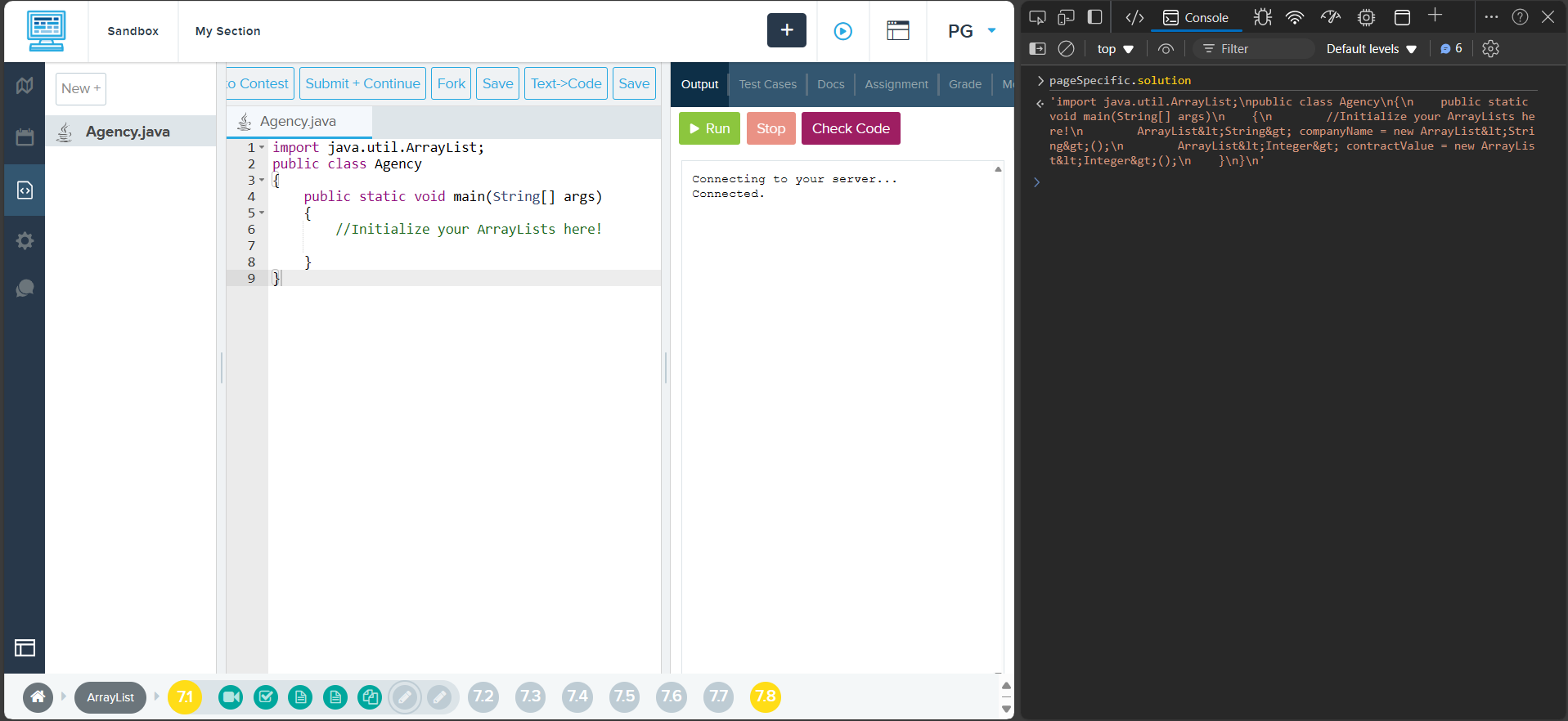
The way this works is simple. The server has a database of solutions that work for each Practice Problem. When a student opens a practice problem, the server embeds a solution into a JavaScript tag in the HTML. This solution is then mapped to the window.pageSpecific object, which is accessible from the browser’s developer tools.
Solution
To fix this exploit, CodeHS should not send the solution to the client at all. Java Practice Problems are run on the server, so the server should check the student’s solution against the correct solution and return a response to the client. This way, the student cannot access the solution without actually solving the problem.
Exploit 2: Deletion of logged-in user’s account
Despite CodeHS not allowing students to delete their accounts, I have discovered a way to delete a logged-in user’s account. This exploit could be used maliciously to delete the accounts of other students, causing them to lose access to their progress, achievements, and other important data. This could have serious consequences for students who rely on CodeHS for their coursework and grades.
CodeHS leaves their account deletion endpoint open to the logged-in user, which is a major security flaw. It is important to note, students cannot delete other people’s accounts. Only their own account can be deleted. Proof of this is attached below.
 The server return a Forbidden response when trying to delete another user’s account.
The server return a Forbidden response when trying to delete another user’s account.
Solution
To fix this exploit, CodeHS should disable the account deletion endpoint for all students. Students should not have the ability to delete their accounts, as this could lead to accidental loss of data and progress.
Exploit 3: Practice Problem Submission without Validation
CodeHS allows students to submit their solutions to practice problems for review and feedback. However, I have discovered a way to submit solutions without actually solving the problem. This exploit could be used to submit incorrect, incomplete, and empty solutions, misleading educators and negatively affecting the accuracy of student assessments.
The issue specifically is that it is the client sending two requests to the server, one to validate the solution and another to submit the solution. The server does not validate the solution before accepting the submission, allowing students to bypass the autograder and submit any solution they want.
Solution
To fix this exploit, CodeHS should validate the student’s solution on the server before accepting the submission. The server should check the solution against the autograder and only accept submissions that pass the tests. This way, students cannot submit incorrect or incomplete solutions, ensuring the accuracy and integrity of student assessments.
Exploit 4: Unauthorized Access to Autograder
Similarly to the first exploit, I have discovered a way to access the autograder for a practice problem without completing the exercise. This exploit could be used to test solutions without actually solving the problem, allowing students to cheat and gain an unfair advantage in assessments and tests.
Just like the first exploit, the server sends the autograder to the client, which is easily accessible through the browser’s developer tools. This is a major security flaw, as it allows students to test solutions before attempting the exercise themselves. It can also be used to reverse-engineer the autograder and create solutions that pass the tests without actually solving the practice problem.

Solution
To fix this exploit, CodeHS should not send the autograder to the client at all. Java Practice Problems are run on the server, so the server should check the student’s solution against the autograder and return a response to the client. This way, the student cannot access the autograder without actually solving the problem.
Special Thanks
I would like to thank the CodeHS team for their prompt response to these exploits. They have acknowledged the issues and are working on implementing fixes to prevent these vulnerabilities from being exploited in the future. I encourage all users of CodeHS to remain vigilant and report any security concerns they encounter to the platform’s support team.
I would also like to thank my AP Computer Science A teacher, Dr. Gamble, for encouraging me to explore the security of educational platforms and for providing guidance throughout this process, as well as allowing me to test these exploits in a controlled environment.
about the author
Pablo Gracia is a high school student from California. He is passionate about technology and music. He is the creator of this blog and the author of all the posts. He is also the creator of the Supernova Experience.
View more blog posts
