Bluebook & Windows Security
May 19, 2025
5 minute read
This is not a guide to bypassing security measures. Everything mentioned here is theoretical and should not be attempted in practice. No one, to my knowledge, has ever executed this during an exam. College Board has been made aware of this vulnerability.
I am intentionally vague about the steps to take in order to bypass the software.
Bluebook is a secure testing application developed by the College Board that is used by SAT and AP tests to take online exams.
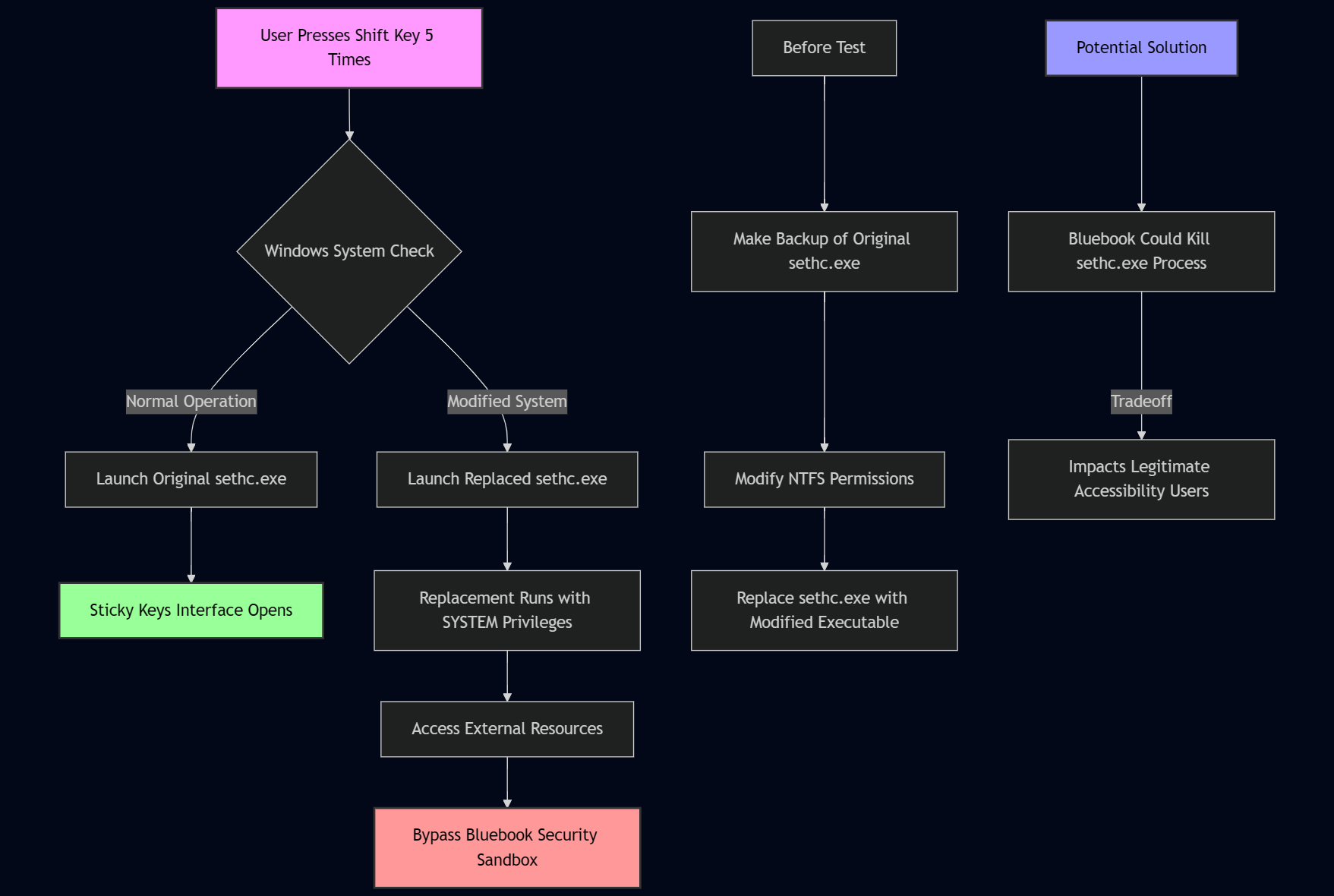
sethc.exe
sethc.exe, short for “Sticky Keys,” is a Windows accessibility feature (Ease of Access in win10), designed to help users with physical disabilities. This executable is located in the C:\Windows\System32\ directory and is launched when a user presses the Shift key five times in a row. When activated, it prompts to enable Sticky Keys.
At its core, sethc.exe runs with SYSTEM-level privileges, which is the highest level of access in Windows operating systems. Microsoft implemented this design to ensure that users with disabilities can access necessary accessibility features regardless of their login status.
Application to Bluebook digital exams
The sethc.exe accessibility feature could be used as a method to bypass security restrictions in locked-down testing environments like Bluebook. This works through a technical process called “binary substitution” that takes advantage of Windows’ execution architecture.
To begin, a user running an administrative session replaces the original sethc.exe file with a copy of another executable. This could be a lightweight resource access tool or browser executable. Typically browsers launch separate processes, so this would not work without heavy modification.
Critical to this technique is maintaining the original file attributes, timestamps, and digital signature information. This is typically done through specialized file operations that preserve metadata while changing the underlying binary code. It is important to note that the replacement executable must be small enough to fit within the original file size constraints of sethc.exe to avoid detection by file integrity checks.
During the exam, pressing Shift five times appears to the system as a legitimate attempt to access an accessibility feature. Windows looks for and executes the file named “sethc.exe” without having Bluebook verify its internal contents beyond basic execution checks.
Detection is nearly impossible
This method is difficult for testing software like Bluebook to detect for a few reasons:
Bluebook process monitoring would only see sethc.exe running, which appears in logs as a standard Windows accessibility process. The process ID, name, and path are legitimate to automated monitoring systems.
The Shift key sequence that triggers the process is a standard Windows accessibility feature. It is impossible to distinguish between a legitimate accessibility request and an intentional trigger of the substituted program.
Because Windows executes sethc.exe with system privileges, the process runs outside the security sandbox that Bluebook establishes for the testing environment, giving it access to resources that would normally be restricted.
Even if monitoring software detected unusual behavior from sethc.exe, the activation happens so quickly that by the time a detection algorithm processes the anomaly, the requested resource would already be accessible.
Technical Implementation Details
The technical implementation requires a few steps:
-
A copy of the original
sethc.exeis created to restore system functionality later. -
System file protection must be temporarily disabled through modification of NTFS permissions on the System32 directory. This could be done through Windows Security.
-
The new executable is copied and renamed to
sethc.exe. It replaces the original in the System32 directory.
From a technical standpoint, this method exploits a fundamental architectural decision in Windows where accessibility features are designed to bypass security restrictions to ensure availability to all users.
Solution
Sometimes, the best solution is to look at what similar products do. Lockdown Browser, for example, immediately kills the sethc.exe process once the window is drawn. This is a simple solution that would prevent the use of this method. However, it is not a perfect solution, as it would also kill any legitimate use of the sethc.exe process. This would negatively impact the experiences of users who rely on accessibility features.
which is probably worth the tradeoff of better test security.
about the author
Pablo Gracia is a high school student from California. He is passionate about technology and music. He is the creator of this blog and the author of all the posts. He is also the creator of the Supernova Experience.
View more blog posts